Browsing the World Wide Web is not as easy as it seems… One wrong click and all your passwords (CERN, Facebook, PayPal, Amazon, etc.) could be stolen; all your activities could be clandestinely monitored (mouse movements and clicks, words typed, screenshots, microphone and webcam recordings, etc.); confidential documents could be stolen; and an attack path (a so-called back-door) into CERN could be opened… As a result, you would have to reinstall your computer from scratch and change all your passwords! One of our colleagues learned this the hard way. One wrong click in summer 2015 permitted malicious attackers to infiltrate CERN but, fortunately, no real damage was done. Still, the cost of investigating the incident ran to several tens of thousands of Swiss francs and a lot of time was wasted trying to understand the attacker’s intent and the extent of the infiltration...
With the goal of increasing more awareness of the risk of clicking on links in unsolicited e-mails, the Computer Security Team recently re-ran the “Clicking Campaign”, sending fake e-mails to you and your (our) colleagues, intended to lure you into clicking on the embedded link. Once an unfortunate, imprudent victim clicks, they are led to an informative webpage explaining “how to identify malicious e-mails” (see the image). Of course, this click rate is proportional to how sophisticated and well-targeted the e-mail is: the more convincing the look and content of the e-mail, the higher the probability of a click (up to a point where a distinction is possible only by experts). Therefore, in order not to be biased (we can easily design e-mails which you will definitely click), we reused the fake e-mails designed for us by students at the University of Rotterdam for last year’s campaign. Then, their boundary condition was to use only information that is publicly available from CERN’s webpages or from their own imaginations. Still, the results were frightening. Some suggestions were so well-designed that more or less everyone at CERN receiving them would have clicked. Experts would call this a sophisticated and targeted attack, a so-called Advanced Persistent Threat (APT). In the end, we selected five fake e-mail suggestions that we deemed to be basic, simple and "easily" identifiable as malicious by the recipients…
The click rates, however, told a different story. Once more, we got an average click rate of 18% (comparable to last year’s number)! One in five recipients clicked on the link… If those e-mails had been real malicious messages, clicking would have meant: computer infected, all local activities monitored, password stolen, data lost and an attack platform into CERN opened. That one click could have had severe operational and financial consequences for CERN... So if you fell for this scam, and our sincerest apologies if you did, let us explain to you how you can better identify such e-mails and what consequences clicking on such a malicious link might have for you and your digital assets:
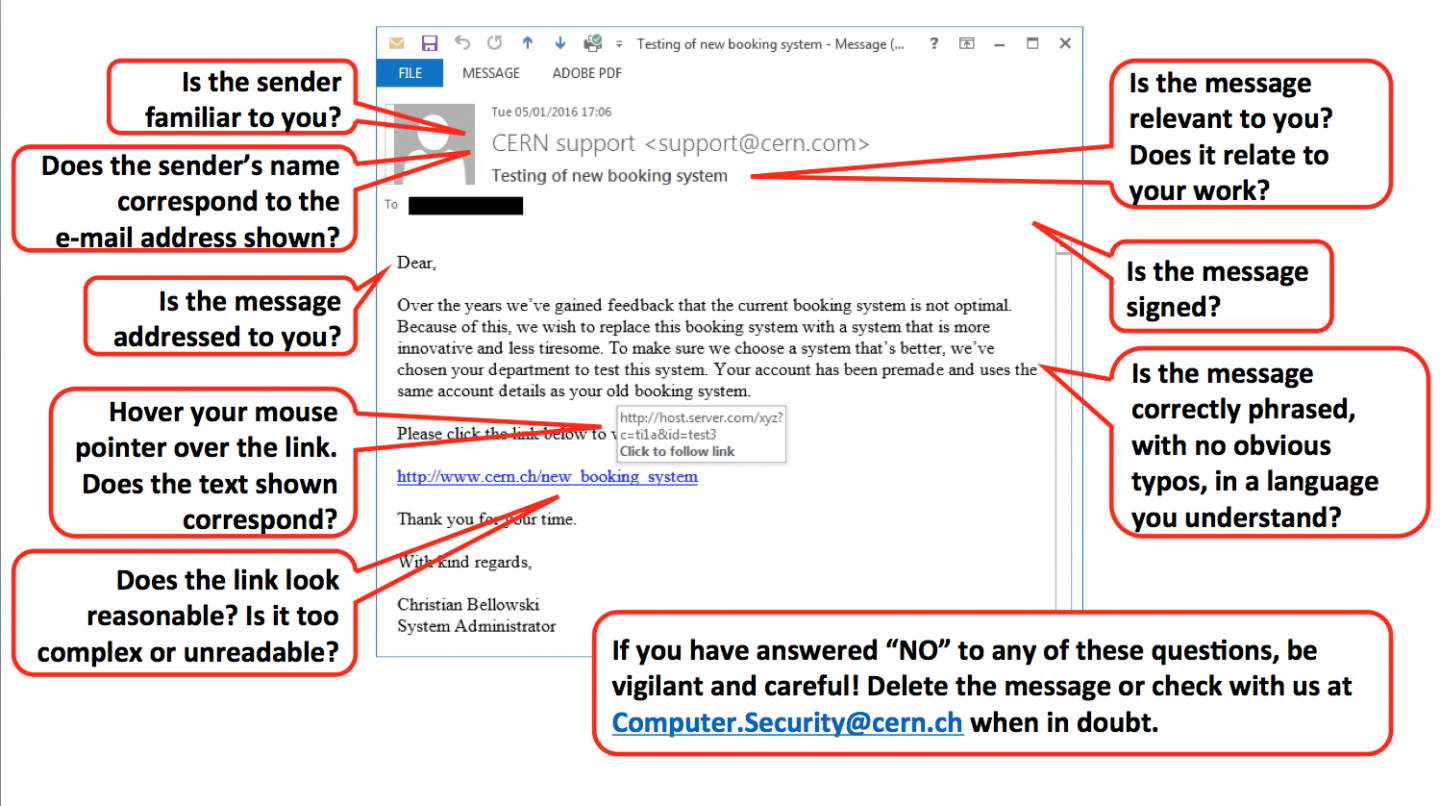
On the positive side, many people identified those fake e-mails for what they were: malicious. We got hundreds of ServiceNow tickets notifying us of "some malicious mails going around". Well done, folks! In any case, stay vigilant and take care. Only click once you are sure. If you are in doubt, contact us at Computer.Security@cern.ch.
And keep in mind: we might run a similar campaign next year with some more sophisticated e-mail messages…
Do you want to learn more about computer security incidents and issues at CERN? Follow our Monthly Report. For further information, questions or help, visit our website or contact us at Computer.Security@cern.ch.
