Mid-May has seen a big weekend for the cyber-threat landscape, as "WannaCry" (also known as "WannaCrypt") came onto the scene with a bang and affected many Microsoft Windows systems worldwide. Using an old exploit developed by the US National Security Agency and published by the ShadowBroker hacker group, WannaCry tried to infect non-patched PCs. As Microsoft has already provided fixes to this underlying vulnerability, this shows once more the importance of patching…
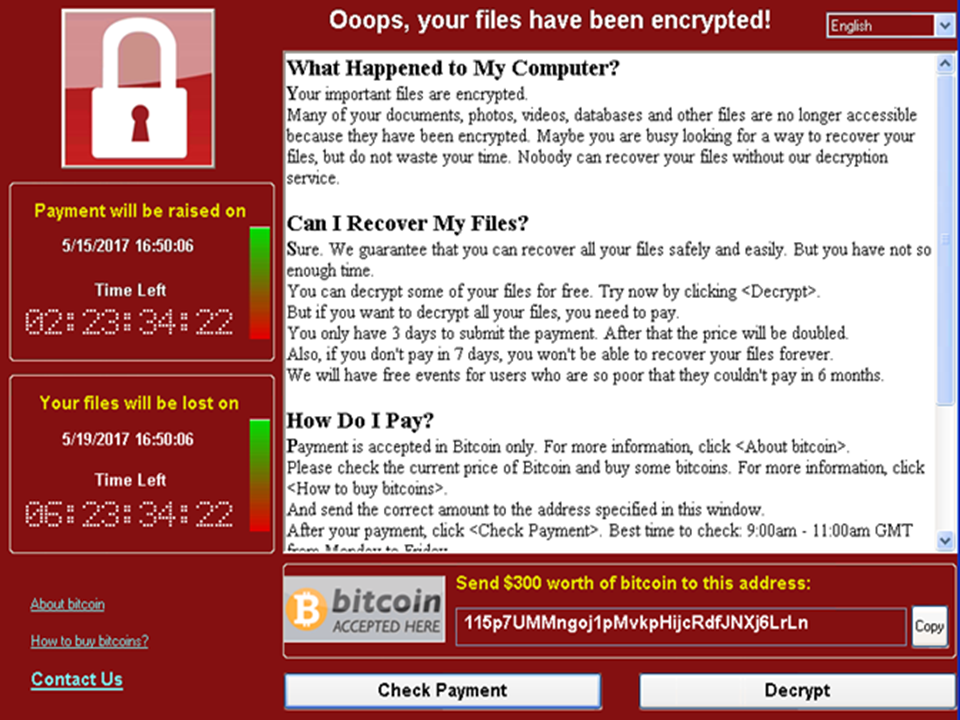
What if you haven’t patched? WannaCry installs ransomware (“Ransomware - when it is too late...”), i.e. software that encrypts a wide variety of files hosted on the computer, including MS Office documents, photos, films, etc. – hence the alias “WannaCrypt”. It also tries to identify external storage systems connected to the PC in order to encrypt those files, too. Unless you have a recent unaffected back-up, the only way to recover the files is to pay the ransom of 300 USD (see photo). Even if the ransom is paid, there is no guarantee that the attackers will provide the decryption details…
How can we fight WannaCry? Like any other malware, the primary infection vector is e-mail (also see our Bulletin article “One click and BOOM… (Reloaded)”). The motto “Stop - think - don’t click” therefore applies once more. Fortunately, this time, the CERN e-mail system and its anti-spam filtering identified and quarantined potentially malicious incoming e-mails. More importantly, all centrally managed Windows PCs were already patched against any exploitation of that kind. Microsoft made the corresponding updates available in March 2017 (i.e. MS17-010). The early bird catches the worm! So no harm was done to those computers. For non-centrally managed PCs, patching should be done regularly; a little effort today could save you tons of headaches in the future. Hence our recurring plea to you to keep your Windows, Linux or Mac computers, and also your Android and iOS smartphones and tablets, up-to-date using their auto-update features (see for example our Bulletin articles “Agility for computers” and “Android is the new Windows”). Windows Update, Mac’s Software Update and Linux’s YUM auto-update are an essential first line of defence of your computer. Running decent antivirus software adds to this: the native Windows Defender (and probably all major antivirus software) was able to detect WannaCry from the beginning. CERN’s anti-virus solution is available to you for free for download and use on your home computers. In fact, the few infected computers this time were sub-optimal private laptops owned by people temporarily visiting CERN. Too bad for them if they didn’t have reasonable recent back-ups of their local files... In the end, as luck would have it, it turned out that the creators of WannaCry had included a “kill switch” inside their code. The kill switch tests successful connection to a certain domain name on the Internet, and, if it exists, WannaCry will not execute. This kill switch was quickly identified by a security researcher, who then ensured that the domain name existed. Connections from inside the CERN network to that domain are redirected to a website maintained by the CERN Computer Security Team thus preventing the devices from being infected and giving us visibility into the affected systems.
For more on this subject, join us for the “Ransomware: Trick or Treat” seminar on Thursday, 1 June 2017 at 2 p.m. in the IT auditorium (31 3-004): https://indico.cern.ch/event/639653/
Do you want to learn more about computer security incidents and issues at CERN? Follow our Monthly Report. For further information, questions or help, visit our website or contact us at Computer.Security@cern.ch.